The Globe and Mail has put up a high quality version of the CSEC (Communications Security Establishment Canada) Presentation that showed how they were spying on the Brazilian Ministry of Mines and Energy. The images are of slides for a talk on “CSEC – Advanced Network Tradecraft” that was titled, “And They Said To The Titans: «Watch Out Olympians In The House!»”. In a different, more critical spirit of “watching out”, here is an initial reading of the slides. What can we learn about how organizations like CSEC are spying on us? What can we learn about how they think about their “tradecraft”? What can we learn about the tools they have developed? What follows is a rhetorical interpretation.
What’s In a Title?
I begin with the title, which has intrigued me as it refers to the Titanomachy, or mythological war between the Titans, a first generation of gods, and the Olympians, like Zeus, child of the Titan Cronos. It is an oedipal story as Cronos kills his own father Uransus to then in turn be beaten by his son Zeus who has been protected by his sister/wife Rhea. In the presentation the Olympians refers to Olympia, the Canadian Network Knowledge Engine (software) that is the topic of the presentation. The suggestion is that the Canadians are the Olympians and they are now in the house, wherever that is, and who are the Titans? Could the Titans be the Americans who came before (and own the house) and to whom a Canadian was presenting or are the Titans the “bad guys” the Five Eyes are all spying on and trying to beat? I wish I could find the source of the quote, I’ve tried in English and French, but no luck. Anyway, the title communicates a certain enthusiasm from the underdog. Attention! The next generation of spying is here and it comes from the smaller nimble human gods.
Another detail that intrigued me is the image on the title slide. After much Googling I found it. It shows an early Olympiad from a 5th century BC Greek vase. The original image is from the Hulton Archive / Getty Images. (One wonders if they got permission to use it, or just copied it off the Internet.) This image suggests another reference for Olympia – namely the Olympics and the elite athletes who compete at them. I’m not sure the slide designer was thinking about this so much as just finding an image for the slide.
One last detail in the title is the use of guillemets or angle quotes (« and ») in the title. Guillements are what the French (and some French Canadians) use instead of inverted commas (quotation marks.) It takes a certain amount of work to figure out how to enter them if you don’t use them as they are a special character not on the English keyboard. Could these slides have been prepared by a Francophone or someone with a Francophone keyboard? Could the quote, “Watch out Olympians in the house!” be a translation of a French reference?
Slide Design
The design of the slides is not interesting. The CSEC author chose a fairly bland slide design. They have taken one of the standard slide Themes from Powerpoint (the image above shows the different Layouts available for this Theme). By contrast the American slides tend to have fancy overwrought graphics.
For example, here is a slide from a presentation on XKeyscore reported in the Guardian. Notice the subtle globe in the background and custom logo. No Greek vase black figure copied from somewhere.
Here is the upper portion from one of the slides released about PRISM festooned with logos, including that of PRISM itself. The Americans are willing to pay for graphic design, even if rather pedestrian.
Finally, here is the upper portion of a slide on SYNAPSE from the New York Times. Note the dendrites reaching into the slide.
In sum, the design is understated and with a classical reference on the first screen. Most of the slides just hold screen shots (that would have been hard to read) with explanatory titles in CAPS.
The Context of The Slides
Now for the context of the presentation. Who was it for and what point was the presenter trying to make? As mentioned above, the June 2012 presentation was designed to demonstrate a “Network Knowledge Engine” called Olympia developed by CSEC and to show how to use it through a case study that involved spying on communications by people at the Brazilian Ministry of Mines and Energy (MME).
One wonders why they chose this case study? Is this indicative of CSEC targets? TV Globo’s Fantástico show, which broke the story thanks to Glenn Greenwald, quotes him to the effect that CSEC must be involved in economic espionage. (I should add that Fantástico seems to have access to more documents than just the slides.) The Globe and Mail elaborated on this in an article here and the Guardian has an article documenting meetings with energy companies. The Guardian got redacted documents using freedom of information requests that seem to confirm an economic agenda to CSEC.
Who did CSEC present this to? According to Fantástico this presentation was given at an annual intelligence gathering of the “Five Eyes” (the United States, United Kingdom, Canada, Australia and New Zealand) who are known to collaborate on intelligence. Snowden, from whom the documents came to Greenwald, was apparently at the conference, though it isn’t clear if he heard the actual presentation, or just got the deck. Why would they present this at this conference? The Globe in this article quotes a military historian to the effect that the Canadians are good at analysis:
“The NSA is intercepting the equivalent of four Library of Congresses every hour,” U.S. military historian Matthew Aid said. “One of the things Canada does very well is analysis.”
The Five Eyes intelligence agencies must be scrambling to figure out how to actually analyze the fire hose of data they are collecting. CSEC’s Olympia may be a genuine improvement on other tools, perhaps because it allows one to chain processes from other tools available from the Five Eyes. (More below on this.)
One anomaly worth noting is that there are differences between the original slides shared by Fantástico (available from Cryptome) and the slides shared by the Globe and Mail “in collaboration with Brazil-based American journalist Glenn Greenwald”. Both decks came from Greenwald, both contain slides not in the other, though the Globe deck has more. In particular Fantástico shows a slide, not in the higher quality Globe set, about how they got information about the “target’s handset” including the model of handset (ie. Motorola MURQ7).
Note also how there seem to be a lot of part of this slide that are whited out. It could be that there is information on this slide that the Globe was convinced shouldn’t be shared while Fantástico just redacted the slide.
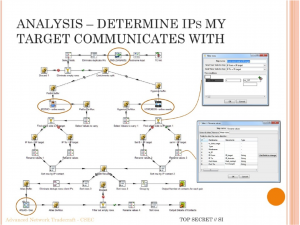
Another anomaly is between the versions of this slide on “Analysis – Determine IPs My Target Communicates With”:
The left slide is from Fantástico and the one on the right is from the Globe. I can’t quite figure out why the title and image would occupy less relative space on the Fantástico version. Even the text has wrapped differently suggesting the title field was resized or font size was changed from one to the other. Perhaps the Globe “improved” the slide for us before exporting. Note at the bottom left of the Fantástico version that there is the shadow of the semi-transparent Powerpoint control bar. This bar of icons is available when you View Slide Show so you can annotate a slide or advance. This suggests the Fantástico version was captured from a projected presentation rather than exported from a Powerpoint file, which may also explain the quality difference. I’m guessing that in both cases they (the media company and Greenwald) were concerned about giving us access to any version of the slides that might have come from the original deck as there might be hidden data retained in exporting. By photographing the presentation, or by grabbing screens, one could ensure that nothing but what you see was in the resulting file.
The Hermeneutics of SIGINT Tradecraft
Now back to the case study. The second slide says that this is a “New target to develop” and that they had “Limited access/target knowledge” which suggests that CSEC wasn’t actually spying on the Brazilians before this case or was pretending to for the purpose of the presentation. The case study (of the MME) could therefore have been chosen more because it showed how to develop knowledge about a new target than because CSEC was really interested in MME. (If I am right then all the fuss about Canada spying on Brazil could be an overinterpretation of the slides.) Either way, what the presenter wanted to show was how Olympia could be used for a project starting with a new target – how it could be used to investigate someone from scratch about whom they had little knowledge. This makes this slide deck particularly interesting compared to others leaked by Snowden that show screens of results or screens out of the context of tradecraft. This presentation walks us through the craft of using the tools at hand to learn about a target starting, on the third slide, with an overview of the questions that
- How can I use the information available in SIGINT data sources to learn about the target?
- What can I find to help me inform efforts to develop access?
- Can I automate the analytical process and / or reuse analyzes created for other purposes?
These questions are revealing of a logic to SIGINT (Signals Intelligence) spying, at least as it is presented here and encoded in tools. The first question is one of interpreting what you have from signals intelligence (as opposed to other human forms of intelligence.) The second question suggests that SIGINT results can and are used to develop other forms of access. In fact the last two slides talk about three ways they can move forward once they have the basic information or BPoA (which others guess means Backdoor Point of Access) from Olympia. These ways forward include human intelligence, passive gathering of data, and tricks like Man in the Middle or Cookie-Replay attacks. The last question then steps back and asks if a process done by hand can be programed for reuse and the answer is “yes”, Olympia includes a process programming environment.
These questions seem to me to be the SIGINT analogue to what we ask when using some document to interpret a phenomenon (like using leaked slides to interpret how intelligence agencies go about spying). We start by asking what the document before us can tell us. Then we ask if there is information in the document that could help with other hermeneutical tactics or with the interpretation of other documents. Finally, if a process for extracting useful information is repeated often, we can ask if it could be automated so we don’t have to do it over and over. Could the close reading of leaked intelligence documents be done on a larger scale?
The Interpreter’s Interface
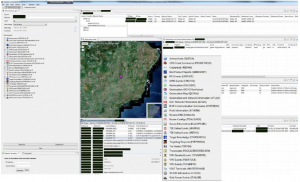
The next two slides show a complex and busy interface with numerous panels, most of which seem to be tables of data. The presenter obviously has a large screen to be able to open all these tabbed panels, but what are they and what is the presenter trying to show? I find it hard to read the labels and text on this screen so this is speculation, but first of all, I think the presenter wants to show how you can get all sorts of different types of information on the screen at the same time. I’m guessing this can be customized by the user (more on this in a moment.) The presenter also wants to show something interesting, so a map of Brazil is smack in the middle with a marker where the capital Brasilia is located. It looks to me like a version of a Google map, but I can’t be sure. My point, however, is that the presenter chooses to put something graphical in the middle of what would otherwise be a rather boring image of lots of tabular data.
A hint as to what the tabbed panels might be comes from the column of items on the left with check boxes. This list is repeated in a way that is readable in the middle of the screen in what looks like a pop-up menu triggered by clicking on something. I’m guessing the presenter wanted to show how you could access this important list of tools from other panels and therefore produces a before and after slide. (Screencasts haven’t made it into CSEC yet.) The list on left, traditionally a place where initial decisions are made in an interface, has some of the check boxes checked including one for “Geolocation Map (QUOVA)” which I suspect is the tool that generated the IP Geolocation Map in the centre. Quova, according to the Wikipedia is now Neustar IP Intelligence, which provides services for identifying the location of web visitors based on their IP address. The other tools listed include:
Anonymizers (QUOVA), CNO Event Summaries (PROMETHEUS), Credentials (PEITHO), End Product Reports (SLINGSHOT), FFU Events (LEVITATE), GPRS Events (STRATOS), Geolocation (EVILOLIVE), Geolocaiton (GCHQ Geofusion), Geolocation Map (QUOVA), Geolocation and Network Information (ATLAS), GoC Network Information (ATLAS), IP-IP Communication Summaries (HYPERION), Ports Information (ATHENA), Reverse DNS (DANAUS), Routher Configs (TIDALSURGE), Survey Information (BLACKPEARL), TDI Online Events (MARINA), TDI Online Events (PEITHO), Target Knowledge (STARSEARCH), Targeting Requests (PEPPERBOX), Tor Nodes (TRITON), and Traceroutes (PACKAGEDGOODS/ARK) …
I may have transcribed some wrong, and I haven’t entered them all or looked them all up. Many appear in other leaked slide decks and in job ads for intelligence analysts (like this one) which suggests that they are standard tools that the audience would have been familiar with. It is worth noting that through Olympia one can access tools from Canada, the USA (Marina) and the UK (GCHQ Geofusion). Note how Olympia is a different interface to a set of tools that the Five Eyes have access to. Presumably there are other interfaces too. It would be fruitful to go through the tools in detail, but that is for another read. In the meantime I speculate that the tools with Classical Greek names (Olympia, Prometheus, Peitho, Atlas and so on) are Canadian tools.
Visual Programming for Spying
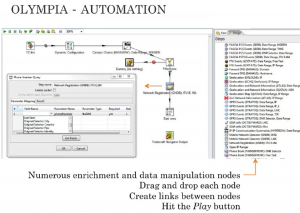
What does Olympia do that is special if it is drawing on other tools. Well one special feature is the visual programming environment provided for automating processes that might use multiple tools. This automation feature is the answer to the third question the presenter asked. (It is always a good idea to ask questions you want to answer.)
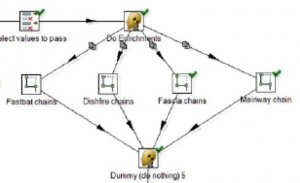
In this visual programming environment users can create “Chains” of processes and “Play” the chain with different input. The fifth slide shows how one has all the tools seen in the first couple of screens available as nodes in a network graph or pipe-and-flow type of programming environment. Such pipe-and-flow visual programming environments have a rich history – they match how Unix developers can quickly put together complex processes from the primitive ones provided by the operating system. You drag out the nodes, create links between them and “Hit the Play button” to run the process.
Why would CSEC put all this work into a visual process flow design environment like this? My guess is that intelligence agencies like CSEC are trying to make it easier for analysts to package up chains of activities so that they can save time and share them with others. My guess is that many analysts are overwhelmed by the proliferation of tools and don’t have the programming skills to code interpretative chains. A common move is to try to make scripting available in a visual drag-and-connect environment that is easier for non-programmers to use.
The chains, as Olympia calls them, show up elsewhere in the slides as it is possible to save a chain as a single node/icon that can then be dropped into other chains. This presumably allows complex processes to be packaged for others in a way that hides the complexity.
Chained Intelligence
It is beyond me to try to interpret the individual chains or processes shown in the rest of the slides, as interesting as that would be, partly because I just don’t know enough (yet) about the phone and IP communications technologies being spied on. I do, however, think this type of close reading is (one thing) we should be trying to do in the digital humanities. These documents were designed for rhetorical purposes and therefore should be read that way. They describe how spies gather and interpret data using tools they make or tools from industry, something (again) that we have experience thinking through. Others will and should question the legality and the politics of what is being done, we in the humanities can contribute by trying to interpret the traces of activity leaked. We have experience with the careful interpretation of incomplete evidence and we know about the we can be careful not to overinterpret or, for that matter, fetishize these interpretations.
I am tempted to close with a joke about Prometheus bound by the chains of Vulcan (one of the Olympians.) How do tools like Olympia constrain their users? Could our intelligence services be investing so heavily in SIGINT that they neglect HUMINT (human intelligence) or overinterpret what they get? Could they come to believe that all there is to know is what is revealed by signals intelligence? The second to the last slide says that “Based on the information collected, I am better positioned to analyse my target’s telecoms environment.” My question would be whether knowing about their “telecoms environment” is really that important or worth it? Setting aside the legalities, did CSEC actually get useful information from this target and for what purpose? As ProPublica has asked about the NSA, there seems to be little evidence that all this intelligence is actually helping. I hope someone with access asks whether good old traditional spycraft works better. In the meantime, Watch out, humanists are in the house!